One of the most common scams you will encounter in your day to day lives is a phishing scam. These can vary from very clever and intricate emails made to look like they have been sent by a genuine company or tailored to your own specific details, all the way down to a basic your great-great-grandmother twice removed has left you a £1 million inheritance (spoiler alert… she hasn’t!).
In the UK, Phishing attacks are by far the most prevalent cyber security concern. Phishing scams account for over 80% of cyber security attacks, coupled with a staggering 90% of data breaches originating from phishing (learn more about Data Breaches in Scotland by reading our recently published blog).
Due to how common these attacks are, we thought we would let you all know the warning signs to watch out for when receiving some form of communication you’re unsure about. Hopefully, the below information will stop you, or a close relative or friend of yours, from becoming victim to a phishing scam.
Most Common Phishing Scams
Phishing attacks can come in many shapes and sizes. Scammers are always innovating their illegal strategies to allow for the highest level of success; however, there are various tactics that are most commonly used.
Here are the most common phishing attacks, according to the very trusted and well-informed source, IT Governance:
1. Email Phishing
Phishing attacks via email have been the most common form of attack since its creation. With over 4 billion active email users across the globe, the ability to have as many addresses as you like, and the incredibly easy set-up process, email is a haven for scammers to prey on their victims. Due to the nature of emails where links are commonplace, it’s relatively easy to convince an unsuspecting person to click on a dangerous link.
The scammers will often use highly recognisable organisations for their domains, such as Amazon, Paypal, Royal Mail (in the UK), high street banks (Barclays, Lloyds, Royal Bank of Scotland, etc.) or other well-known organisations. These domains are used for two reasons:
- The recipient is going to trust the email far more if they recognise the sender’s address
- Due to their high volume of customers/users, the recipient is likely a genuine customer/user of the organisation, prompting an increased reason to click a link
There are two other recognised forms of targeted, socially engineered email phishing we should discuss. If you work in a workplace that the communication relies on email, keep a note of these.
Spear Phishing Attacks
More personalised forms of Email Phishing attacks can occur if the attackers have gained access to your contact address through a leak or hack – this is known as Spear Phishing. If the attack has information to connect you to a certain organisation, this can help make their email appear to be more genuine. Scammers can conduct Spear Phishing attacks if they have the following information:
- Name
- Connected organisation (employment, education, charity, etc.)
- Email Address
- Specific information about involvement in organisation (job title, subject of study, etc.)
An example is, if an attacker knew you were a student of Glasgow University, they could send you an email that required you to click a link to view a change in your study schedule. Once the incredibly genuine-looking link is clicked, the attack is successful.
Whaling Phishing Attack
Whaling attacks are similar to Spear attacks, in which the target(s) are contacted via email, and high volumes of sensitive information are required. However, Whaling attacks specifically aim at scamming high-profile individuals within an organisation e.g. executives, management, etc. while imitating senior staff.
Another element that distinguishes Whale Phishing from other forms of Phishing, is that there’s a heightened focus on deceiving its victims into performing actions, such as wire transfers. The attack is successful as employees will be more likely to perform actions when said action is requested by a senior member of an organisation.
2. Phone Phishing
Phishing scams aren’t only conducted via email. With the massive increase in mobile users, more and more scammers have begun to focus their attention on Phishing attacks via text messages (Smishing) and phone conversions (Vishing). We will cover both forms of Phone Phishing below.
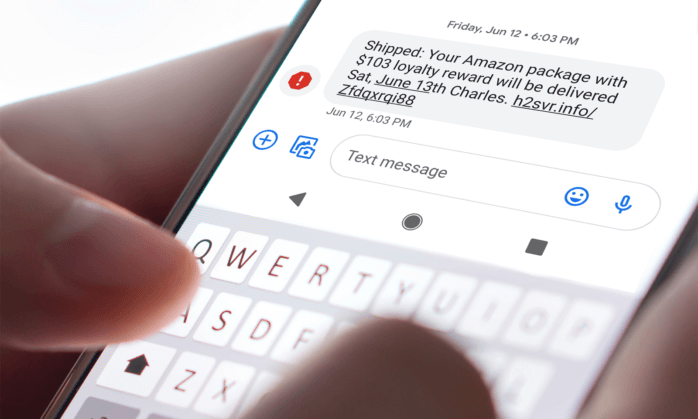
Smishing
SMS Phishing, or Smishing, is the act of phishing via text messages. SMS is one of the most popular forms of communication between businesses with existing or potential customers. These attacks are usually in the form of well-known and trusted organisations such as banks and will include either Malware or a malicious website within the sent link.
Smishing is becoming an effective way for successful attacks due to the trust we hold in text messages. Phishing scams are well-known to occur via email, so when someone receives a Smishing text, we’re far less likely to assume it’s a scam (especially if it’s disguised as a trusted source).
Kaspersky has provided some ways to prevent falling for Smishing scams. If you’re unsure of a text you’ve received, do the following:
- Contact the organisation that’s named in the text
- Don’t use the links or contact information on the text message – go directly to the organisation’s website
- Don’t respond to the message
- Check the phone number to find anything unusual, such as a non-UK number
- Don’t, under any circumstance, provide a password or confirmation code via text
Vishing
Voice Phishing (Vishing) is the use of phone calls to conduct a scam. We’ve all received them, sometimes multiple times a day, in which you’re told something like “Your Windows computer has been infected” or you’re offered a “one-time deal” from a well-known organisation.
These Vishing scams are being conducted for the same reason as the others… to get your personal information!
Identifying a Vishing Attack
- Have you won a high-value prize from a competition you’ve never entered?
- Are the callers pressuring you to decide on the call?
- Have the callers threatened you with the prospect of jail time, a fine, or deportation?
- Has the word “Gift Card” been mentioned?
- Is the “Government agency” requesting sensitive information over the phone?
If any of the above points seem familiar, then chances are you’ve been the recipient of a Vishing attack.
Visit the Federal Trade Commission Consumer Advice for more information on Vishing attacks.
3. Social Media Phishing
Also known as ‘Angler Phishing’ this new form of Phishing has become an increasingly frequent issue for social media users around the globe.
The process of Angler Phishing involves fake social media accounts (commonly Twitter & Facebook) responding to users’ queries, requests, or complaints. These accounts will attempt to appear as similar to the organisation’s genuine account as possible. The Phish attack will occur either as a direct message or as a public comment and will involve the user clicking on a link that will either install Malware or lead the user to a malicious website.
How to Protect Yourself from Social Media Phishing
- Do your own research into the account’s information – are they verified? Do they have a high number of followers? Do they have a history of Tweets/posts that appear natural?
- Contact the organisation directly via their official website
- Does the response include a shortened link? Scammers will often use URL shorteners to hide their clearly malicious redirection link
If you believe you’re subject to an Angler Phish, please report it to report@phishing.gov.uk.
If You Think You’re Being Scammed…
Stop
Take a couple of minutes to stop and think. Is it touching on emotion – urgency or trying to influence you? These emails are designed to make you act without thinking, so you want to interrupt that process and give your brain time to think.
Challenge
It could be fake – verify all payment and supplier details directly with the company on a known number or in person. Or if it is an internal email, speak to your colleague in person.
Protect Yourself
Contact businesses bank immediately if you think you have been scammed and report it to them.
Report to the Authorities
Help build evidence to prevent crime in future by forwarding anything suspicious to report@phishing.gov.uk.
What We Can Do to Help!
This is where we can come in with our awareness training and empower your staff to be the front line of your cyber defence as opposed to the weakest link. You can have the best security system in the world, but it can all be undone by the right staff member getting caught out at a bad time.
Further educate yourself and your business from cyber crime with our Cyber Essentials Training. Get your free consultation, today!

